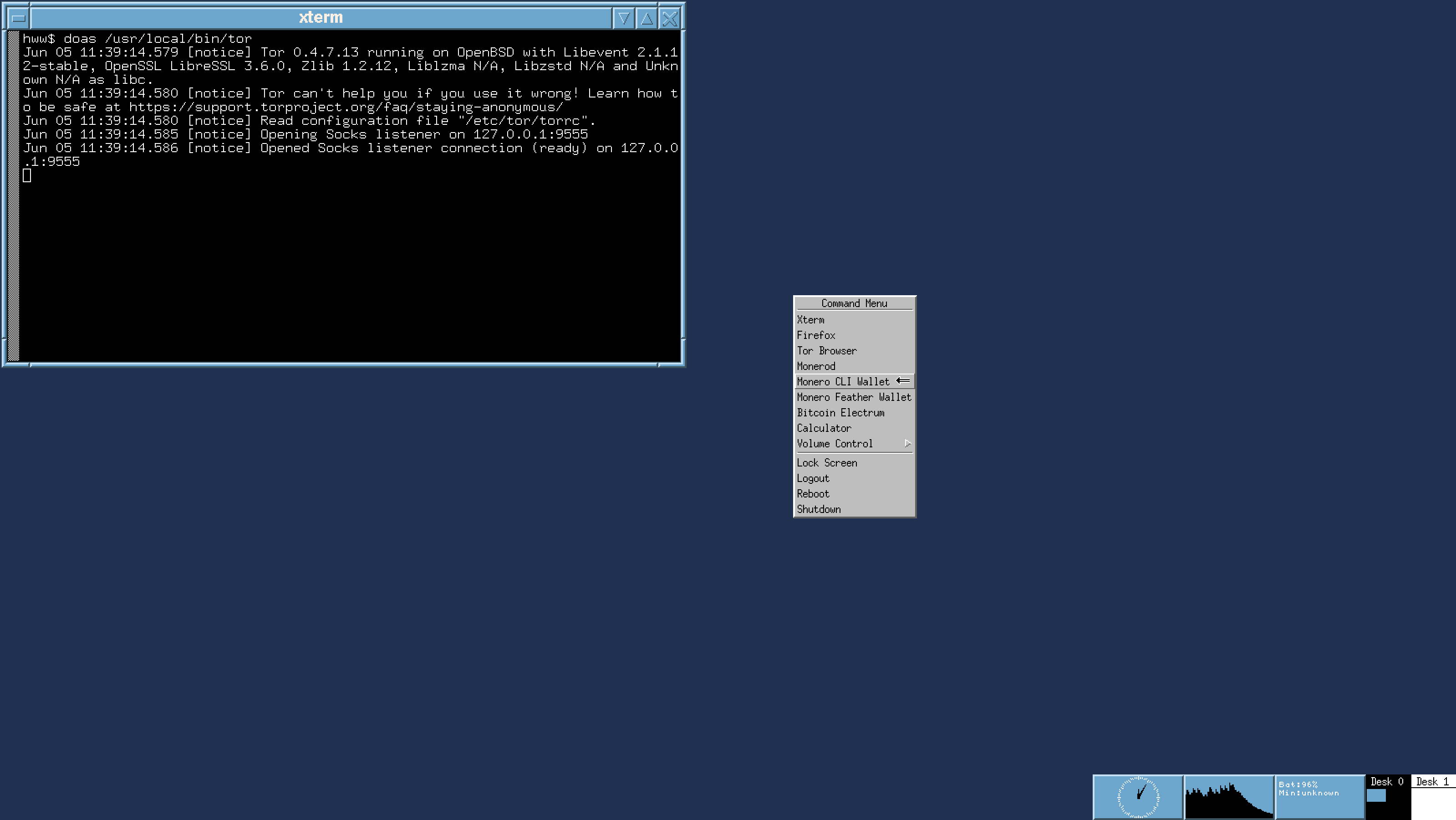
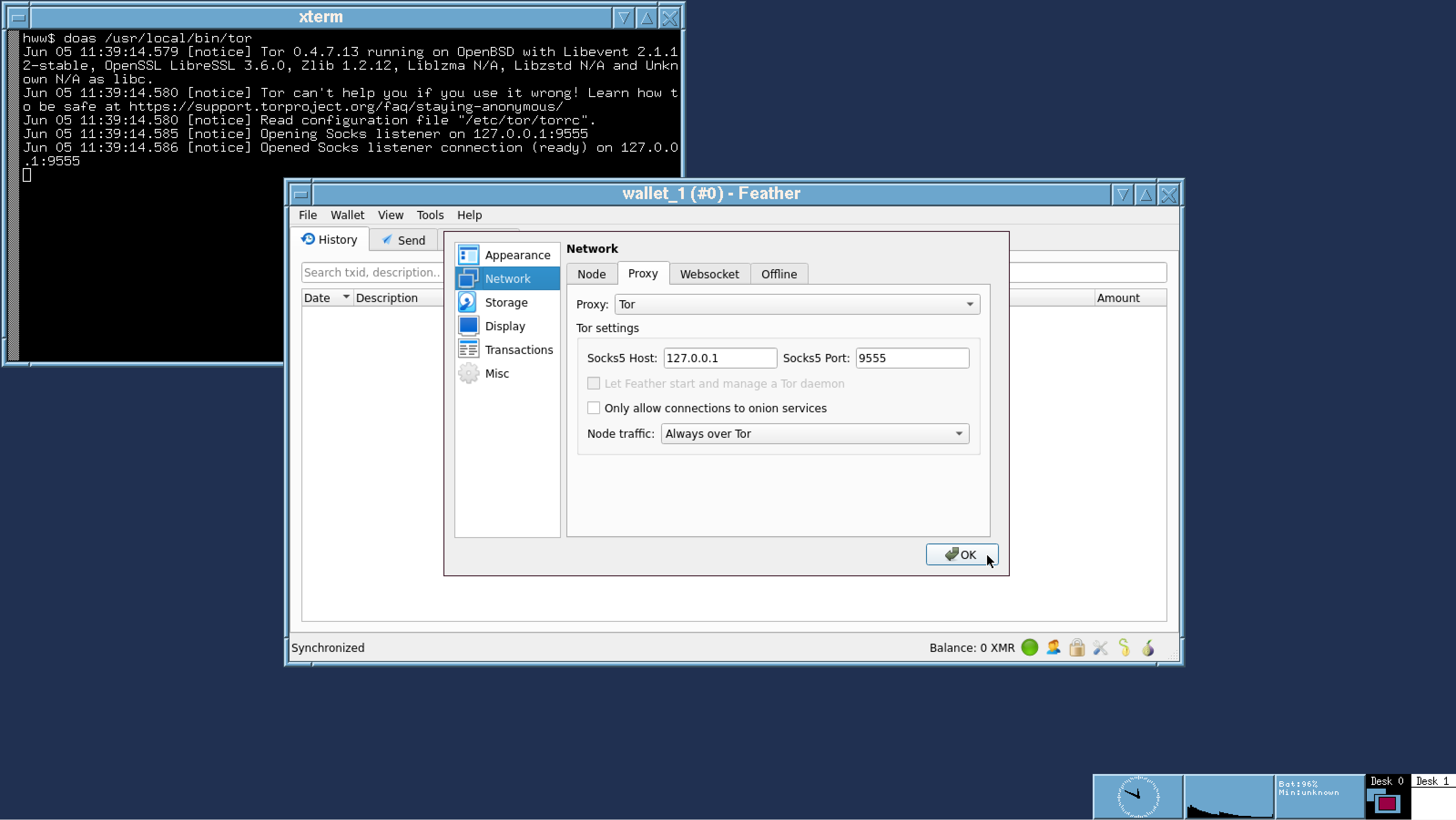
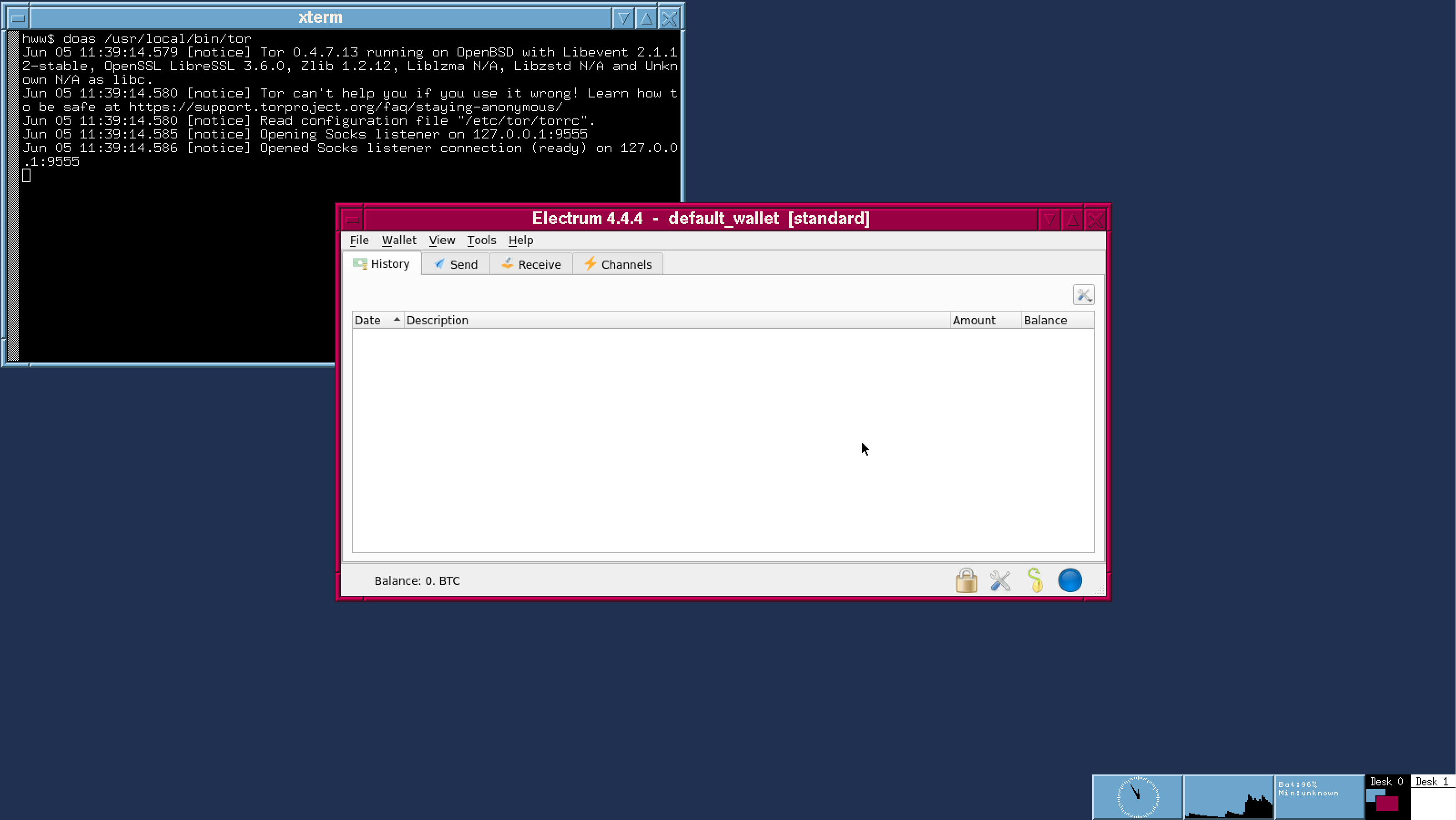
Official Monero CLI suite, Feather Monero Wallet and Bitcoin Electrum are already working. Depending on your wish, they all can be configured to connect the Internet via tor/tor browser only.
The nowadays scandals around Ledger hardware wallet (and inherently all the proprietary hardware wallets) as well as Atomic software wallet (and inherently all the closed-source software wallets) have inspired us to bring the only true fundamental solution for a hardware/software wallet: a dedicated laptop running OpenBSD on a SOFTRAID encrypted disk with disabled Intel ME/AMD PSP CPU manufacturer's spyware. Alternatively one can use a palette of ARM64 dashboards compatible with OpenBSD since ARM processors are typically too simple to have an "ARM ME".
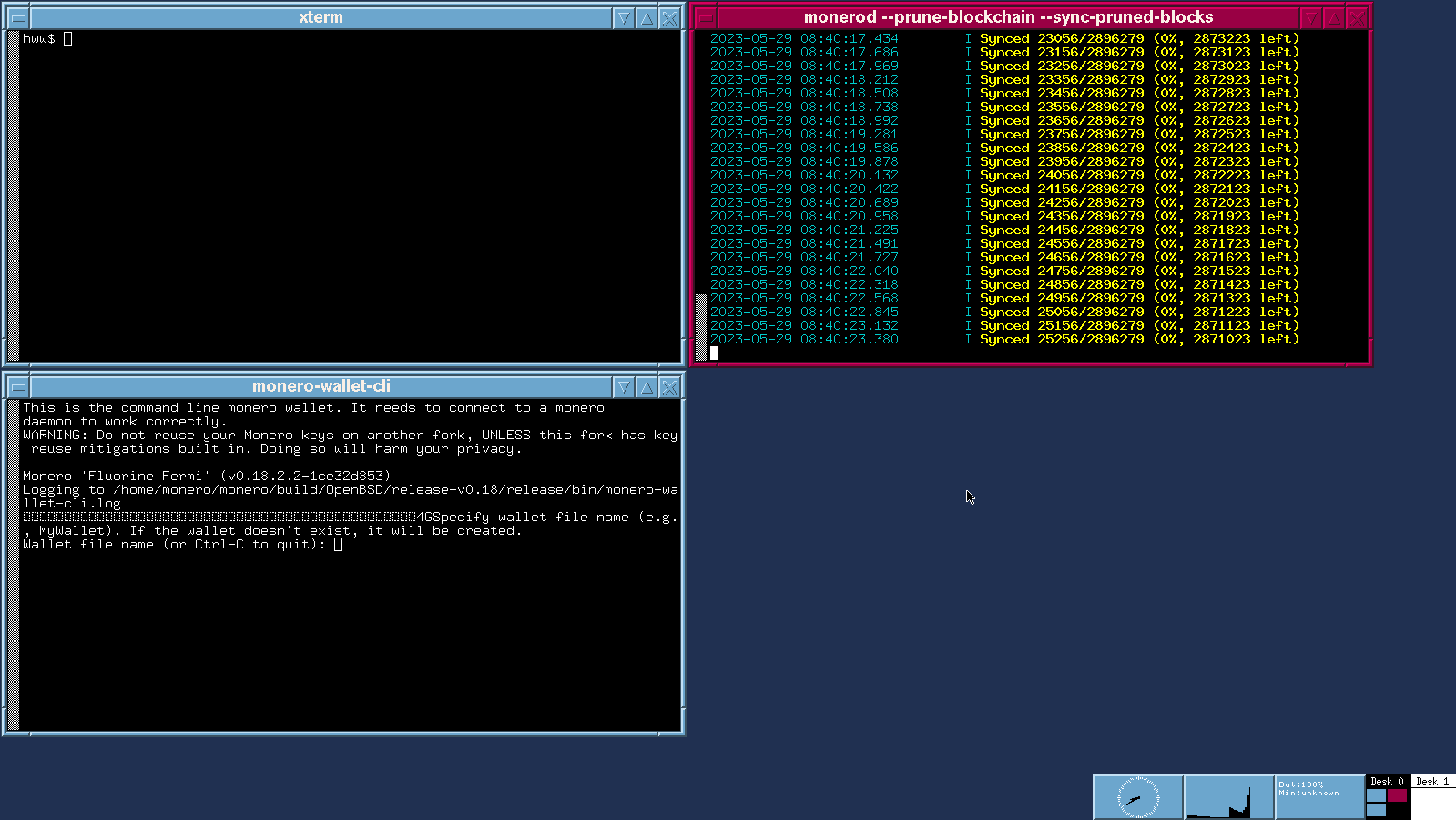
Currently, official Monero CLI wallet has been successfully ported to OpenBSD. Also Bitcoin Electrum and Monero Feather wallets have been ported too. It just needs a time to write the build instructions. Screenshots for them are available now. All the apps work fine via tor/tor browser as well! We strongly believe every advanced crypto user MUST compile the wallet software himself from their open sources, as it is directly required by the entire Crypto philosophy.
Each crypto wallet on OpenBSD will be stored under separate user login and running on the current user's X Window system using original wallet login name. All the wallet users are unprivileged and thus completely isolated from each other. Customer can't accidentally wipe out the software. Also potential malware caught by one login name can't propagate to another one. And of course, customer can't catch a virus, because Firefox and Tor Browser are running from their own login names or even chroot or vmm hypervisor.
The goal of this project is to provide fully automated open source scripts that build the open source wallet software on the customer's dedicated laptop or virtual machine. The whole setup will be as easy as "git clone <repo-name>; make; make install".
In fact, OpenBSD is an easy to use operating system that nevertheless calls a "holly thrill" in a mid customer mind. We are here to break that thrill and bring OpenBSD into the Crypto world as a Gold Standard of the finance security. OpenBSD ships with extremely lightweight yet fully customizable xenodm display manager & fvwm window manager that both can resemble Microsoft Windows in base GUI interactions. VirtualBox OpenHWW images will be available soon for playing and testing purposes.
There are customers that can't dedicate a whole separate computer to serve as a hardware wallet. No problem. They can create and bootstrap a VirtualBox or Qubes OS virtual machine from the same open source install script. Also there will be ready-to-use virtual machine images available for download and testing as well.
What another crypto wallets do you want to be ported and incorporated into fully automated build script on a OpenHWW platform? Write email to: minexmr2@tutanota.com.
 -school cryptos!—
-school cryptos!—